
Using technology to run your business is a no-brainer in this day and age. It speeds up processes, helps employees and vendors communicate efficiently, and provides fast, reliable data about all aspects of your business.
But there are risks when your information is managed online. When it comes to financial operations, companies have to be especially careful to ensure their employees are vigilant, their business practices are compliant, and their finances are ultimately secure.
One of the best ways to protect your financial operations is to know how to spot the methods that bad actors use target your company and how to protect yourself.
As part of International Fraud Awareness Week, we want to be a part of keeping your business protected. Here are three common fraud risks to look out for and how to mitigate them.
Vendor email compromise scams
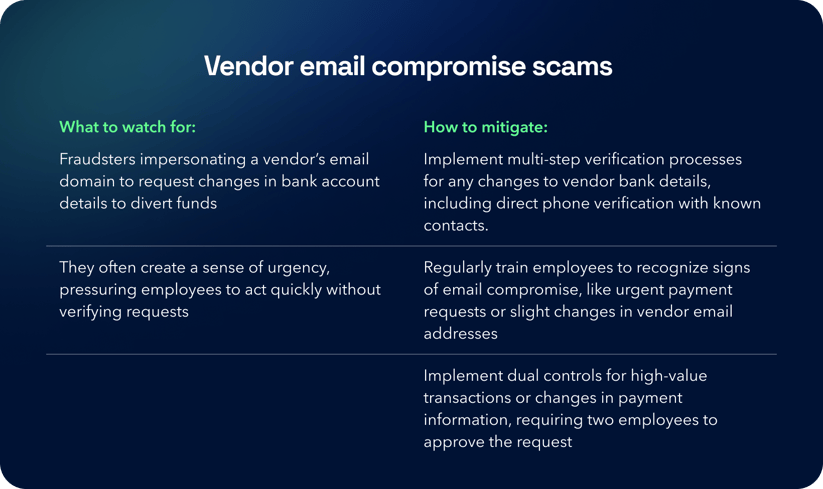
In vendor email compromise scams, fraudsters infiltrate or spoof vendor email accounts. They request unauthorized payments, often posing as legitimate vendors or altering payment instructions to redirect funds to fraudulent accounts.
Account takeover
Account takeover occurs when fraudsters gain unauthorized access to a company’s business or financial accounts. Once access is obtained, they can carry out malicious activities like transferring funds or making unauthorized payments.

Insider fraud
Insider fraud is when employees, contractors, or business partners misappropriate assets, manipulate transactions, or leak confidential information. This type of fraud can be particularly damaging because insiders often have direct access to sensitive systems and knowledge of company processes.

Your security is our top priority
If you’re a Plooto customer and suspect fraudulent activity, email us at [email protected], and our dedicated risk team will take immediate action to protect your account.
Email us









